
I had an email the other day from a website I manage with a security alert:
A user with username “Fred Bloggs” tried to sign in to your WordPress site. Access was denied because the password being used exists on lists of passwords leaked in data breaches. Attackers use such lists to break into sites and install malicious code. Please change or reset the password.
(That wasn’t the real username, by the way!)
Luckily the site was running a security plugin, Wordfence, which caught this login attempt, but it was a little worrying.
After changing the password, I decided that it was time to add an extra layer of security to WordPress, Two factor authentication.
But first, let’s look at how hard – or otherwise – it is to log into WordPress.
How secure is the WordPress admin?
When you log into the WordPress admin, there’s a check for something you know: your username – or email address – and your password.
But a hacker may be able to work out your username or email, and take a guess at your password. Especially if it’s “123456″ or another commonly used password.

Or, they might retrieve them from a list of passwords leaked in a data breach.
Data breaches are not uncommon, though the penalties are greater now that GDPR is in force.
The big problem is for people who use weak passwords, or reuse the same passwords over several accounts.
Imagine you create a new account on a shopping site. The site asks for a password, and to save time you use the one that you use for your website, because it’s easy to remember.
Then one day the shopping website emails you to say,
We’re very sorry, but we’ve had a data breach and your login details were compromised.
So you change your password. No big deal.
Except if you used it somewhere else – like your website’s login page! You might not think to change your password there, and now it’s been exposed, without you realising.
If you use the same combo of email and password over several sites, you might be leaving the door open to hackers on your own website. Share on XIncidentally, you can check if your email address has been involved in a data breach through this site: Have I Been Pwned? You might be quite surprised about what comes up!
What is Two Factor Authentication?
Two factor authentication (2FA) is an extra layer of security when logging into a website.
As well as something you know, you need something you own.

The commonest item to own to prove you are authorised to log in is your mobile phone.
(Another possibility for 2FA is something you are i.e. biometrics.)
If you can’t verify that you are who you claim you to be, you don’t get in: simple as that.
Set up WordPress Two Factor Authentication with Two-Factor
Unfortunately, 2FA isn’t part of WordPress Core (yet). But there are a number of plugins which will do the job.
I used the Two-Factor plugin, recommended by security guru Tim Nash.
Go to Plugins > Add New and search for “two-factor”. I’m assuming you are an administrator of your site, who has the right to install plugins. If not, you’ll need to ask whoever is responsible for managing your site to do this part.
Install and activate the plugin.
Then go to Users > Your Profile. (If you’re not an admin, it’s just Profile).
Scroll down to the Account Management section and the Two-Factor Options part.
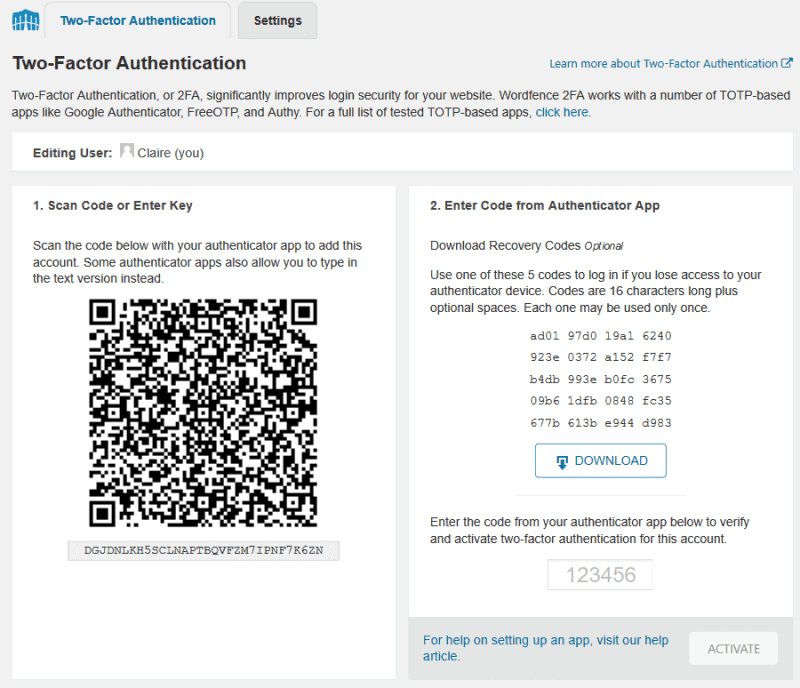
You’ll see a few options to pick from. We’re going to use the Time-Based One-Time Password option (Google Authenticator).
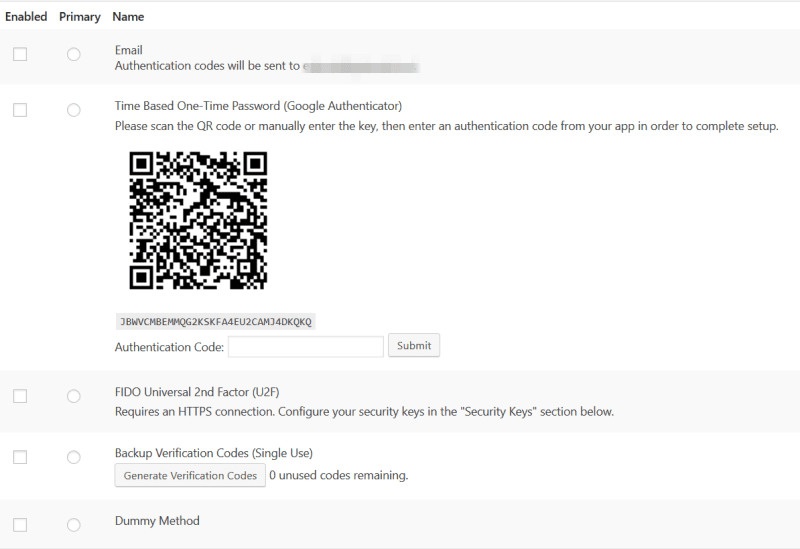
To start, check the Enabled checkbox and the Primary radio button for that option.
Then get out your phone and download and install the Google Authenticator app.
Tap the red + button on the app.
Select an option to scan the QR code or input the key underneath in your app. At this point, it’s a really good idea to take a screenshot of the QR code and key on your computer, before proceeding to the next step.
On the app, you will see a 6-digit code for your site which regenerates every thirty seconds.
Tip: In Google Authenticator the name of the site shows followed by your username or email address. (I’ve blanked them out in my screenshot below.) If you want to change the display of the latter, hold down the entry and then tap the pencil icon to edit it.
Input the code into the Authentication Code field on your site and press Submit.
You should then see a message “Secret key configured and registered.”
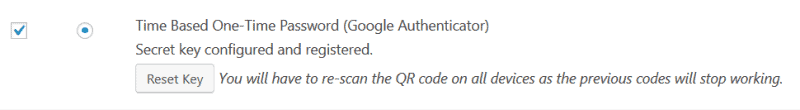
The next time you log into your site, there will be an extra step. After you input your username/email and password, you’ll be asked for the 6-digit code generated by the Google Authenticator app on your phone.
If anyone else tries to log in and can’t produce the right code, they will not get any further.
Does enabling 2FA for one user with Two-Factor enable it for everyone on a multi-user site?
The answer is no: each user must set up two factor authentication for themselves.
What happens if you lose your phone?
You’re probably thinking that this is all fine, until you lose your phone or upgrade to a new one. What then?
There is a way round that. You can set up some Backup Verification Codes which can be used to log in to the site. They act as temporary passwords.
Naturally, you need to do this before your phone is lost, stolen or upgraded!
Go to your profile and enable the Backup Verification Codes option. Then use the Generate Verification Codes button.
You will be rewarded with a list of 10 codes. Keep these in a safe place. I recommend storing them in a password manager.
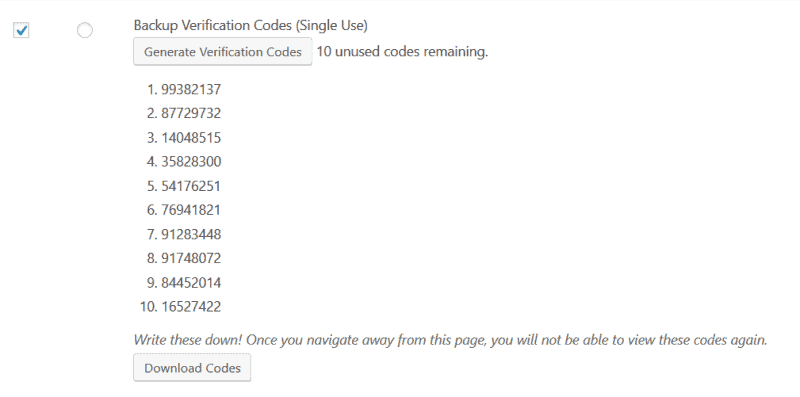
If you misplace your phone, you now have an alternative way to log in. The codes are single-use; once you have used one, it cannot be reused.
I can’t log in at all… what now?
If you don’t have your phone, and have no backup method to log in to your site, as a last resort you can manually disable the Two-Factor plugin. You will need control panel or FTP access to your site. Follow this guide: Disable a WordPress Plugin Without Access to Your Admin Area.
Does Google Authenticator have any limitations?
If you read the app reviews, one of the main complaints is that the Google Authenticator codes can’t be synced to a Google Account.
If you get a new phone or have to do a factory reset there’s no simple way to recover the information stored in Google Authenticator. Some people have had to go through a lengthy process with sites they enabled 2FA on to prove that they are a legitimate user.
This is why it helps to screenshot the QR code on setup, in case you need to connect it to a new device.
What other authentication methods are there in Two-Factor?
There are 3 other means of authentication:
- FIDO Universal 2nd Factor (U2F)
- Dummy method
These can act as your main authentication procedure, or as a backup.
Of those, Dummy method is just for testing purposes. Don’t enable this, because it offers no security at all (you’re simply asked to click a button proving you are you!)
Email sends a verification code to your email address after you fill in the login form, which makes it as secure as your email.
The other method is FIDO Universal 2nd Factor (U2F) . I haven’t tested this out but it requires two things:
- An HTTPS connection (you are using HTTPS, aren’t you?
- A FIDO-compatible device (a security key) which plugs into a computer or laptop via USB.
You need to buy a suitable security key to use U2F. Android 7.0 and above phones are also compatible, as they have the key built-in.
Some people regard U2F as more secure than Google Authenticator’s Time-Based One-Time Password (TOTP) method. For a comparison of the two, read this: Reasons why U2F is better than TOTP (one-time password). (Be aware that this is written by a manufacturer of U2F devices!)
Set up WordPress Two Factor Authentication with Wordfence
If you already use the Wordfence security plugin, it has 2FA built-in. You don’t need to install another plugin.
Go to Wordfence > Login Security to set it up.
Wordfence uses the Time-Based One-Time Password method.
You don’t have to use Google Authenticator, though – you can use any app that supports TOTP.
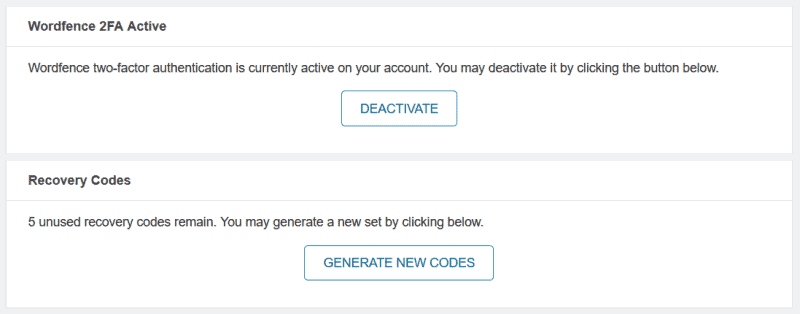
Another difference is that Wordfence’s implementation automatically generates recovery codes for you. You get 5 single-use codes.
After you have enabled 2FA, it’s simple to deactivate it or generate new recovery codes.
Wordfence has some extra settings: you can require 2-factor authentication for all site administrators (allowing a grace period for them to set it up, so they don’t get locked out!) You can also enable 2FA for other user roles.
In addition, to reduce user friction you can set Wordfence to remember the one-time password, so that it only needs input once every 30 days.
Furthermore, you can enable reCAPTCHA v3 on your login page, though that comes with privacy implications.
Help with Wordfence’s two-factor authentication.
Summing up
Two factor authentication is recommended for securing your website and other online accounts that you use. This article has a great summary of why and where you should use 2FA.
I’ve looked at two plugins that offer WordPress two factor authentication. You can find a number of other 2FA plugins on WordPress.org.
Do you use WordPress Two Factor Authentication? Which is your preferred plugin? Have you ever had any issues with it? Let me know in the comments.


Hi Claire
Great post on a very important topic!
Yes, I also use Two-Factor, as recommended by my go-to security guy, the one and only Tim Nash of 34SP. I have been using it for a while now with no issues at all.
That’s good to hear, Mark!
I wish I had read this article a couple of years ago. I had a successful blog for my consulting business that got hacked by a Chinese hacker. I first started noticing posts to it that were nothing but search engine magnets – whole posts full of random words and phrases with high SEO. Sometimes, there would be posts all in Chinese, and, when I would translate them, they were not mine, nor were they related to my site. I would delete the posts, but didn’t know what to do next (I’m a solo operation – no big IT budget). Then I noticed I could not longer log into it. Eventually, I had to close the website down.
I will definitely look into more security options. Thanks.
Oh no – that must have been really hard for you. I had to get my site cleaned up after a hack once, too. You tend not to be complacent after that.
Taking regular site backups is also important, so you can revert your website to a clean version.
Hoping you stay hacker-free in future,
Claire
Two factor authentication is important, but people should be aware that the most common implementation of 2fa (SMS messages) is actually the weakest option. Either an app based solution or a hardware token/key would at least satisfy the “something you have” aspect of 2fa (SMS messages sent to your phone can be redirected).
Good point! Do many 2FA apps use the SMS method?
Yes SMS is very common, but with bodies like NIST suggesting against its use we are likely to see the use of this method slowly drop off (FIDO is probably the most likely to take off right now, but eventually that will probably be replaced too due to its reliance on a USB port).